What Does It Mean For Critical Infrastructure, Manufacturing & Building Management Systems?
Co-written by Ofer Shaked and Maayan Fishelov
Introduction
A new vulnerability (CVE-2020-0796) has been discovered in the SMB compression mechanism which allows a client to attack a server and run arbitrary code unauthenticated. A specially crafted server can also attack a client connecting to it with the same vulnerability. SMB compression has been presented into the SMB protocol in version v3.11.
Affected Services
- SMB Server – A client can send a specially crafted packet containing a data compression feature and exploit the server.
- SMB Client – A malicious attacker can develop a special version of a SMB Server, and when a client connects to it, trigger the vulnerability using a compression mechanism.
Affected Windows Versions
- Windows 10 Version 1903 for 32-bit Systems
- Windows 10 Version 1903 for ARM64-based Systems
- Windows 10 Version 1903 for x64-based Systems
- Windows 10 Version 1909 for 32-bit Systems
- Windows 10 Version 1909 for ARM64-based Systems
- Windows 10 Version 1909 for x64-based Systems
- Windows Server, version 1903 (Server Core installation)
- Windows Server, version 1909 (Server Core installation)
According to Microsoft, older operating systems such as older builds of Windows 10 or Windows 8 won’t be discovered as affected in the future, since the compression feature wasn’t available on them.
The Risks This Causes To Industrial Control Systems
The last time that such vulnerability has been discovered was in 2017, in CVE-2017-0143 (SMBv1), and it wrecked havoc in industrial control systems by ransomware worms exploiting the vulnerability, such as WannaCry and NotPetya. We suspect that this vulnerability might also be used soon in ransomware worms and are advising what can currently be done to mitigate the threat.
What You Can Do About It
The SCADAfence Research Team recommends the following mitigations:
- Detect all affected machines: Using your Asset Management software, detect all instances of Windows that are affected by the vulnerability,
- Use the Microsoft-recommended workaround until a patch is available and disable the SMBv3 compression mechanism (see below).
- Review your network architecture to make sure it’s protected against ransomware worms. This should be done using real information collected in the network rather than using the network diagrams only, because the implementation might differ from the design in dangerous ways.
- Detect malware activity – Vulnerabilities are only one part of the story. Different malware have similar components and methods that can be detected regardless of a specific vulnerability. Use products for malware and anomaly detection that can detect when you’re attacked.
The SCADAfence Platform for industrial cyber security management, allows you to automate your asset management, uncover vulnerabilities in your software and architecture and continuously detect malware activity.
How To Detect Exploitation Of CVE-2020-0796
SMBv3 compression is disabled by default. There’s no documented way to enable this feature. Therefore, any observed SMBv3 compressed traffic should be suspected as an exploitation attempt, since it’s unlikely to be used by legitimate parties.
SCADAfence has added a specific alert when this feature is in use:
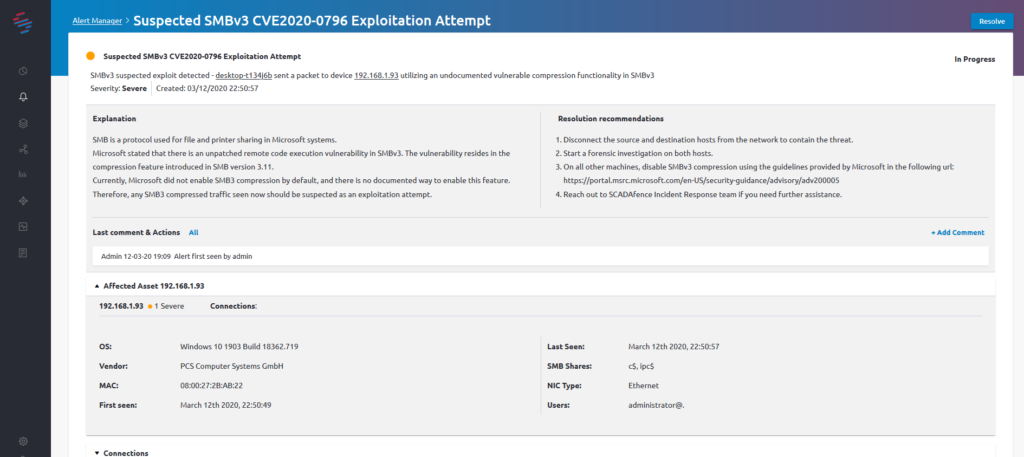
If you see this alert, contact our Incident Response team for immediate assistance.
How To Disable The SMBv3 Compression Mechanism
Set-ItemProperty -Path “HKLM:\SYSTEM\CurrentControlSet\Services\LanmanServer\Parameters” DisableCompression -Type DWORD -Value 1 -Force .
Source: ADV200005 | Microsoft Guidance for Disabling SMBv3 Compression
If you need further help or advice, feel free to Contact Us.

