IoT Device Fleet Management
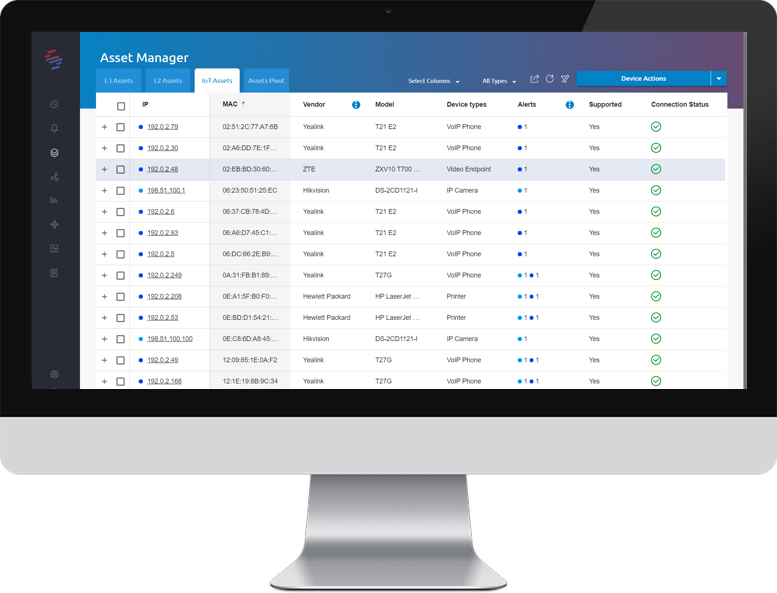
- Automatic inventory of all IoT devices, regardless of vendors and device models
- Detailed device information such as vendor, model, firmware versions and others
- Perform bulk managerial actions on devices
SCADAfence IoT Security is the only agentless, vendor-agnostic IoT security management product. It is capable of managing a deployed IoT device fleet over the network. Whether you use IoT devices as part of a business application or general-purpose IoT such as IP cameras and printers, SCADAfence IoT Security is the right solution for you.
The Challenge:
“IoT Manageability is a throwback to IT of 20 years ago” (Gartner 2019 Planning Guide for IoT)
IoT devices are a central part of the modern enterprise and can be found in nearly every network. Several assessments mention that enterprises may have more IoT devices connected to the enterprise network than workstations and servers combined.
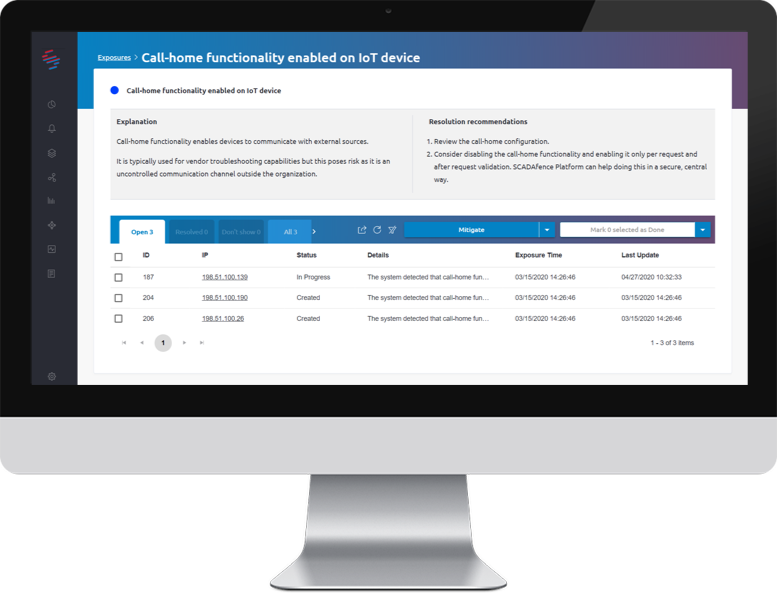
Organizations often have a large number of IoT device models from multiple vendors, with limited security and management options. This low visibility of device information, configurations and device behavior results in an overall low-security level, one that leaves the devices exposed to compromise by malware and hackers.
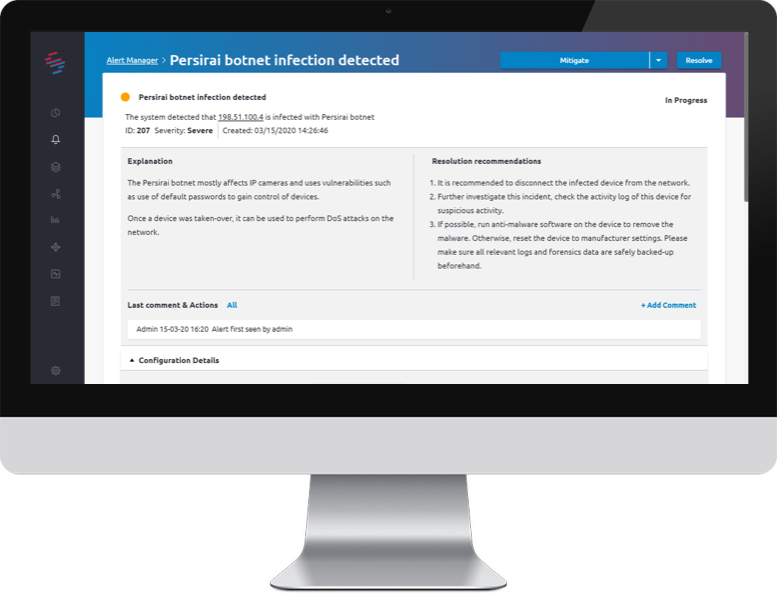
Thus, IoT devices are now a low hanging fruit for attackers, who leverage them for different purposes. Read more on our blog post.