The Governance Portal
Centralized Automated Governance of Industry Regulations for OT & IoT
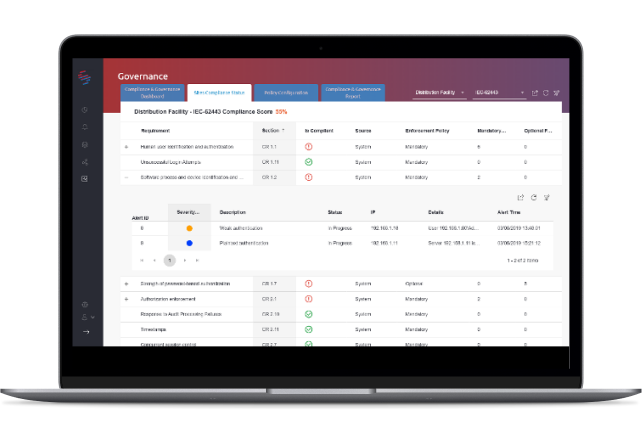
Centralized Automated Governance of Industry Regulations for OT & IoT
Into Networks, Asset Discovery, IOCs and Inventory Management
Risk Management, Cyber Threat Detection & Safety
Test in Minutes, Deploy in Hours, No Impact on Operations
OUR CUSTOMERS SAY THAT OUR PRODUCTS PROVIDE THE HIGHEST DETECTION RATES AND LOWEST FALSE POSITIVES IN THE INDUSTRY
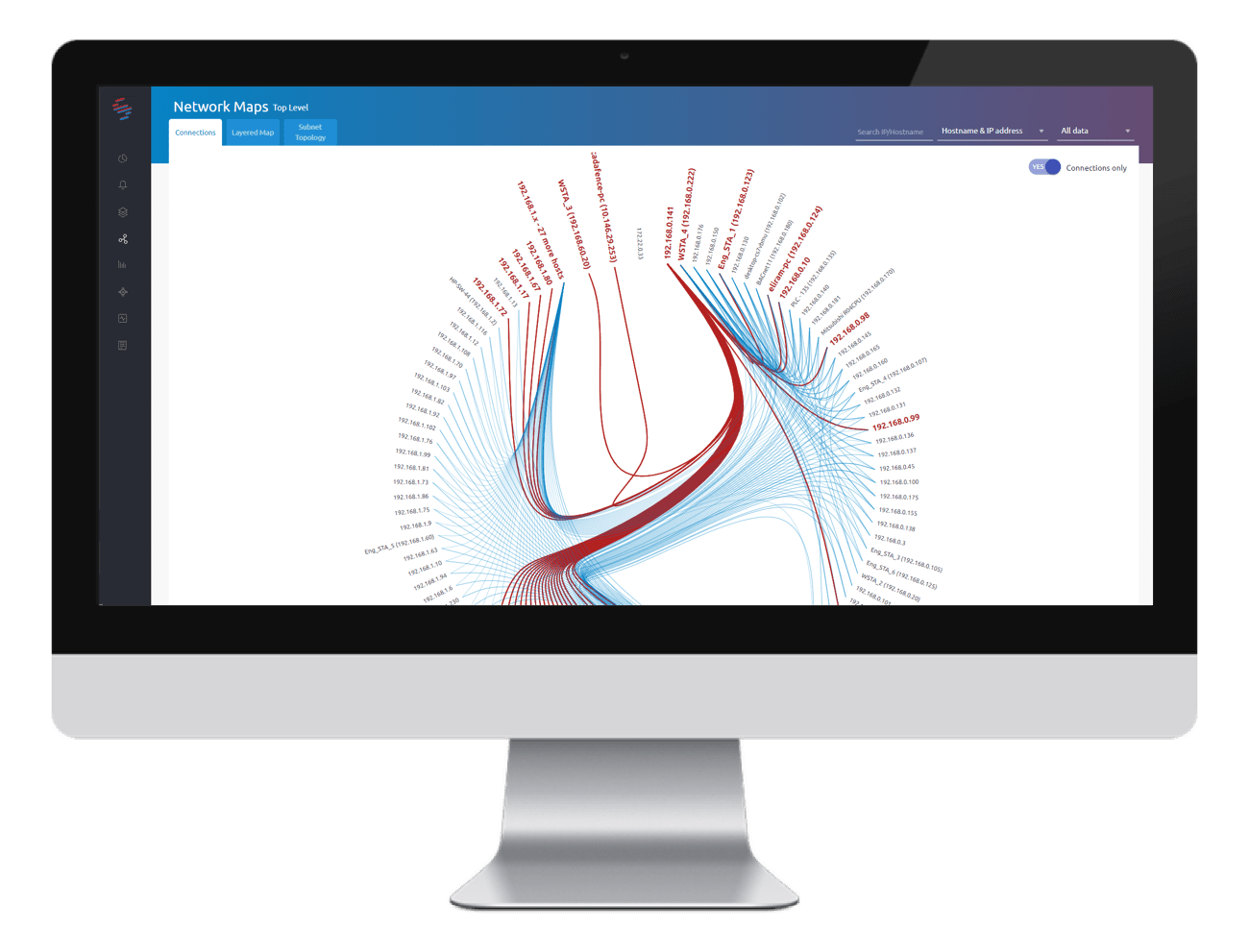

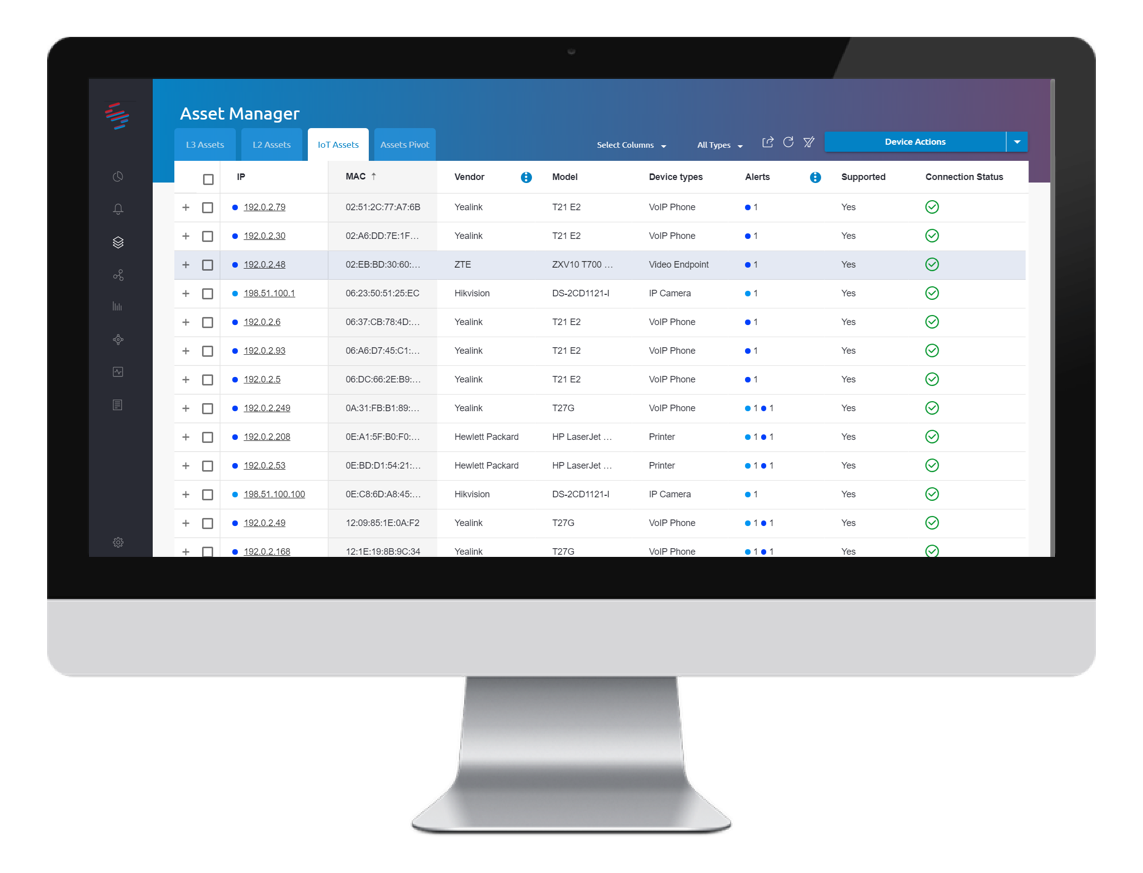

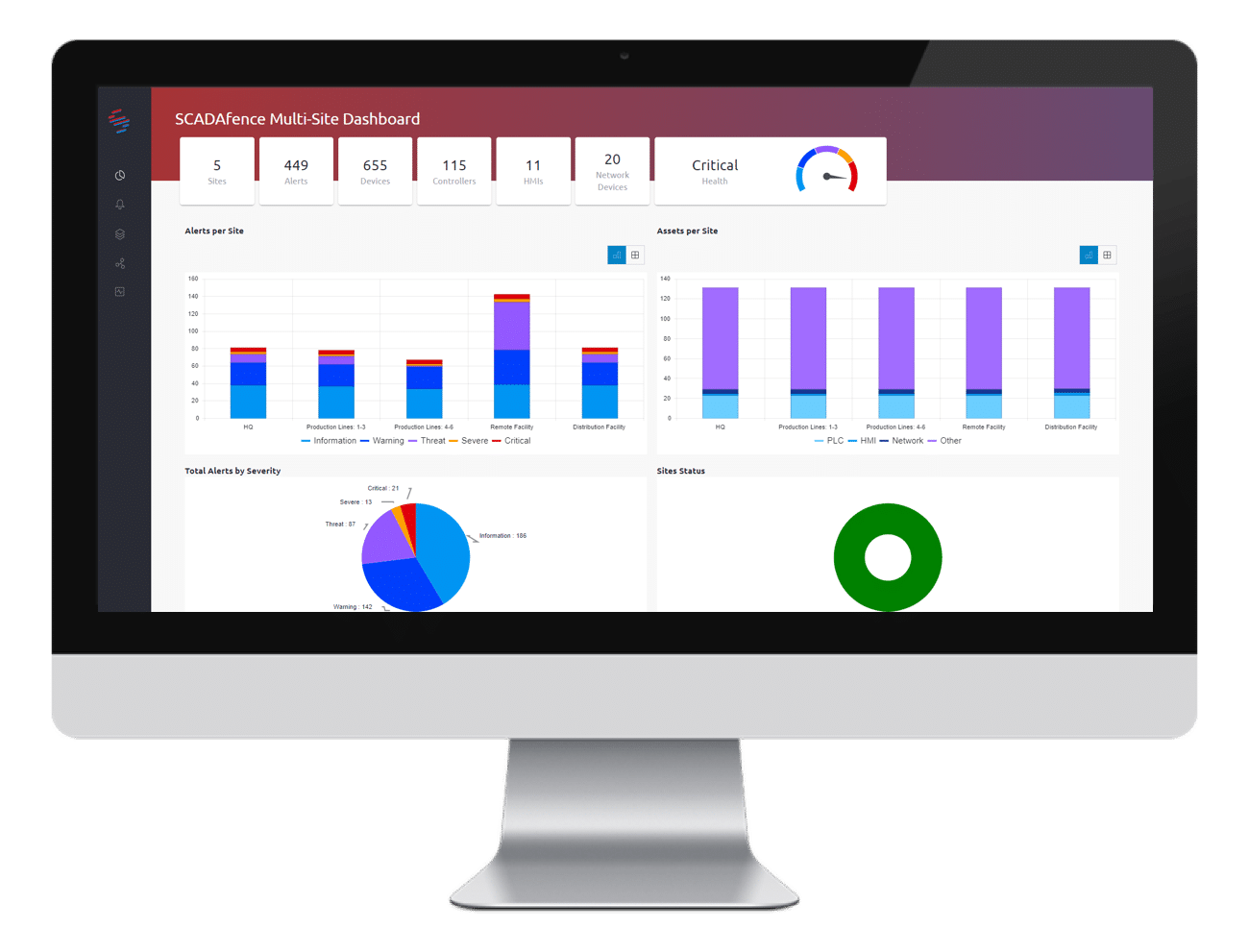

Our Groundbreaking Products Protect Millions of Devices Across Multiple Industries




It’s simple to deploy! Plug & play, no agents, no network latency – up & running in hours!
Our users tell us that we have the highest detection rates in the industry, and we don’t overload them with false positives.
You no longer have to travel for days to your remote sites to check their adherence to IEC 62443, we do it automatically and remotely for you.
You don’t have to deal with hundreds of malfunctioning or quarantined IoT devices, we manage and fix them for you.